Overview
Shinjiru Application Web Load Balancer, with its WAF and DDoS protection features, provides a robust and secure solution for managing network traffic, making it an excellent choice for web hosters. It not only ensures high availability and scalability of applications but also provides advanced security features to protect against web-based threats and DDoS attacks. It’s Kubernetes-ready infrastructure ensured high-availability of your application by monitoring your servers which shared the same DNS and IPs, with one single pointing. Load Balancers are constantly monitored for availability and anomalies—any issues discovered are corrected automatically so your app always runs smoothly. Our service is backed by 24x7x365 management and monitoring by expert support staff, as well as performance-based SLAs, providing comprehensive protection for the network resources that power your business. For more info, please refer to our Pricing Plan.
WAF and Load Balancer Protection Pricing Plan
DDOS Protection Features
API Protection
- Provide SSL
- HTTP/ HTTPS configurable and encrypted
- High availability load balancing based on number of servers connected backend
Web Application Firewall (WAF)
- Allows or blocks request based on rules configuration
- Bot protection and enable threat campaigns
DDoS Monitoring
- DDoS detection is performed using advanced machine learning
- Detect unusually large spikes, sudden drops and other abnormal traffic pattern
Kubernetes Ready
- Handle traffic for the services on the specified virtual address and load-balances to all nodes in the cluster
- Application services proxy
- Monitor changes and adjust load balancer accordingly
Affordable & Easy to Deploy
Shinjiru Offshore DDos Protection has capabilities that makes our DDoS protection service able to deal with all kind of attacks.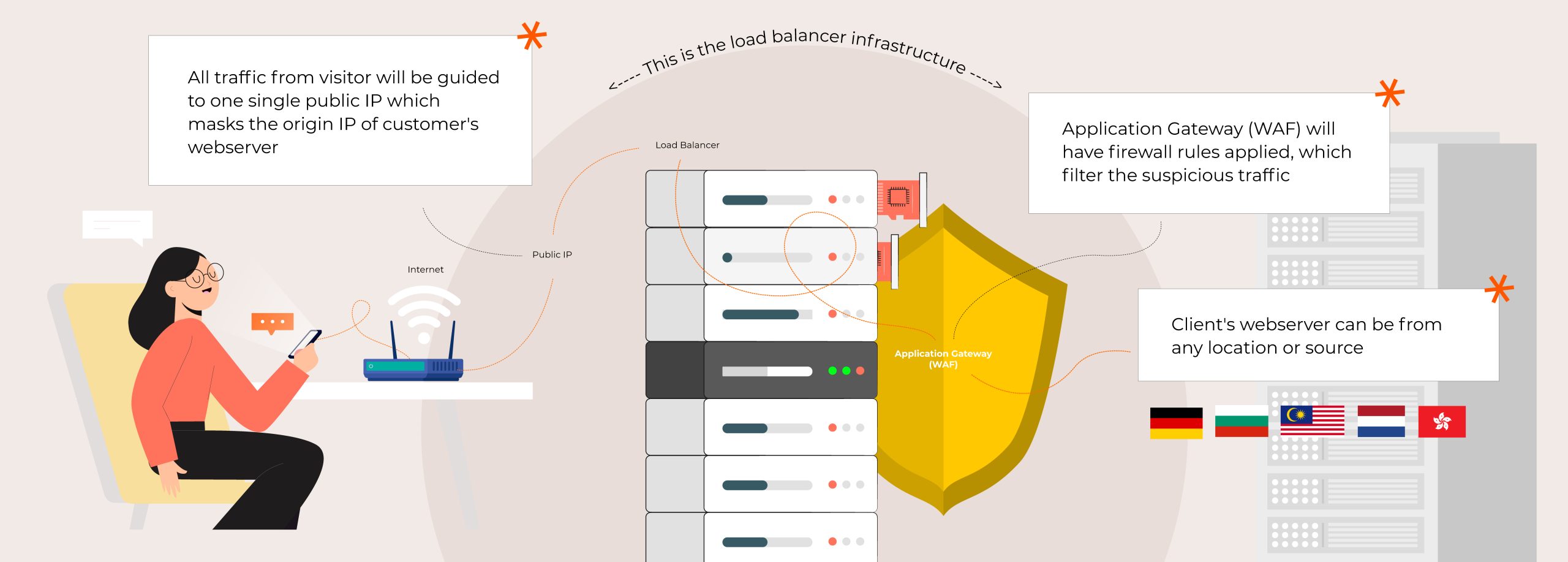
Key Benefits

Be prepared for a range of attacks with mitigation based on maximum attack size, not bandwidth
Bypass traditional, tedious fault-resolution procedures with monitoring and notifications

Ensure business continuity by protecting access to critical resources

Safeguard your customer experience and business reputation

Enjoy lower total cost of ownership against premise-based solutions

Avoid capital expenditures and lost revenue from service outages

Protect last-mile bandwidth and avoid costly over-provisioning

Improve network and application uptime

